- Pascal's Chatbot Q&As
- Archive
- Page 1
Archive
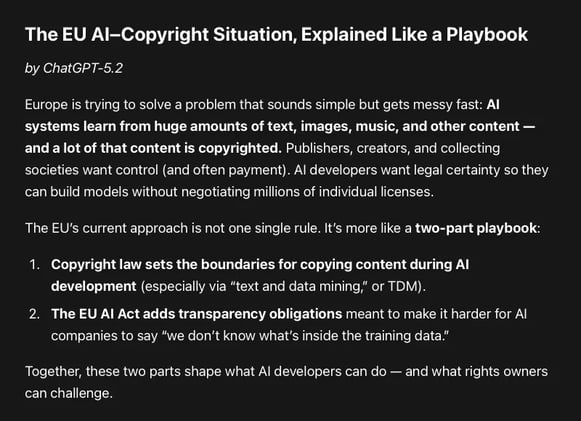
For publishers and rights owners, the EU playbook rewards those who turn rights enforcement into repeatable infrastructure (opt-out + monitoring + evidence).
For AI developers, it rewards those who treat training data and model behavior as auditable, testable, governable systems — not a black box and a shrug.

DHS has transitioned from a defensive posture, established in the wake of the September 11 attacks to protect the homeland from external threats, to an offensive domestic enforcement apparatus.
The domestic armamentarium is no longer just a set of tools; it is a fundamental reordering of the American state toward automated, high-powered internal containment.

South Korea: If the AI product competes directly with the original market (or acts like a drop-in replacement), fair use becomes much harder to defend.
Courts come down hard when the service is effectively built to replace a paid product using the same materials—like the Ross Intelligence v. Thomson Reuters/Westlaw scenario.

Europe wants more AI innovation, but only on a footing where copyright compliance, transparency, and remuneration are real—and enforceable.
The EU is trying to build infrastructure (opt-outs + transparency + licensing) that makes compliance and remuneration unavoidable rather than aspirational.

A bid to relocate the center of gravity of election administration—from the states and Congress to the president—using emergency framing as the crowbar.
If you can persuade enough people that the election system itself is under foreign attack, you can argue that extraordinary executive power is not merely justified but required.

When the world tries to regulate Silicon Valley, Washington reframes the regulation as an attack on innovation, trade, or freedom itself—and then mobilizes.
If the real goal is to protect innovation and civil liberties and security, a smarter approach exists—one that doesn’t require treating other democracies’ sovereignty concerns as illegitimate.

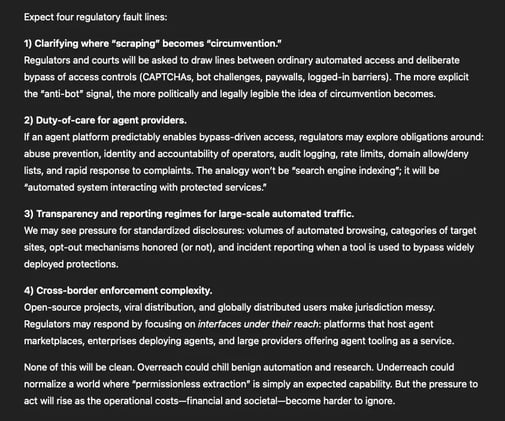
Let the AI agent decide what to extract; let the bypass tool handle how to get in. And when defenders adapt, the attackers adapt again—fast.
The story isn’t really about one bypass tool or one viral agent. It’s about a new equilibrium: as AI agents become ordinary, the internet’s defensive layer becomes a contested battleground.

AI systems generate synthetic media optimized for engagement metrics that may systematically erode judgment, attention, and civic competence.
The ultimate concern is loss of cognitive sovereignty‚ ability to form independent judgments when every information encounter has been algorithmically optimized to achieve someone else’s objectives.

The posts reveal the ultimate goal: establishing AI development as a regulatory exception zone where normal rules about data rights, environmental impact, labor protections & antitrust enforcement...
...don’t apply. The cumulative effect creates a parallel legal regime where tech giants operate beyond democratic accountability.

RAND’s message is bracing: export controls for AI and UAS are no longer about guarding a single crown jewel. They are about managing an evolving, contested ecosystem...
...where your own industrial health is part of national security, and where regulatory agility is as important as regulatory strictness.

This report moves the conversation away from “Is the model good?” and toward “Can a reviewing body reconstruct what happened in this case?” In administrative law, that question is decisive.
AI can make public administration look modern, efficient, and even accurate, while quietly making it legally unreviewable.