- Pascal's Chatbot Q&As
- Posts
- The Goldberg/Martin case will likely serve as a pivotal case study for the next decade of cybersecurity regulation and insurance.
The Goldberg/Martin case will likely serve as a pivotal case study for the next decade of cybersecurity regulation and insurance.
This case proves that the RaaS model has evolved. It is no longer just about “hackers vs. companies.” It is about criminal recruitment within the supply chain.
The Betrayal of the Guardians: A Systemic Analysis of United States v. Goldberg et al. and the Weaponization of Trust in the Ransomware Economy
by Gemini 3.0, Deep Research. Warning, LLMs may hallucinate!
Inspired by this LinkedIn post.
1. Executive Summary
The watershed conviction of Ryan Goldberg and Kevin Martin in the Southern District of Florida represents a fundamental rupture in the trusted operational model of the global cybersecurity industry. These two individuals—credentialed experts employed by elite incident response and digital currency negotiation firms—did not merely succumb to external threats; they became the threat. By leveraging their privileged access, specialized knowledge of insurance limits, and understanding of negotiation tactics, they operated as affiliates for the ALPHV/BlackCat ransomware cartel, one of the most destructive cybercriminal enterprises of the last decade.
This report serves as an exhaustive forensic, legal, and operational analysis of the case United States v. Goldberg et al.. Triggered by the initial post by Michael Tchuindjang, this document deconstructs the procedural anomalies that have fueled industry skepticism—specifically the use of the Hobbs Act over the Computer Fraud and Abuse Act (CFAA), the complex jurisdictional nexus linking Texas and Georgia residents to a Miami courtroom, and the conspicuous absence of the “Third Man” from the primary indictment.
Through a synthesis of court filings, Department of Justice (DOJ) disclosures, and technical threat intelligence, this report argues that the “oddities” identified by observers are not evidence of a “Pravda”-style cover-up, but rather the visible artifacts of a high-stakes federal strategy utilizing cooperating witnesses and 1940s-era racketeering laws to dismantle a modern digital conspiracy. The investigation reveals that the seemingly “single count” plea is a calculated legal maneuver to secure significant prison time while protecting the ongoing intelligence value of the unindicted co-conspirator in Land O’Lakes, Florida.
2. The Catalyst: The Julie Schroeder Inquiry
The modern information security landscape is often bifurcated into two distinct streams of consciousness: the sanitized, official narratives released by government agencies, and the raw, often skeptical discourse that occurs within the practitioner community. It is in this second stream that the true contours of the Goldberg case were first critically examined.
2.1 The Voice of the Community
Julie Schroeder, a CEO and Chief Data Risk Officer1 , served as the catalyst for a deeper interrogation of this case. Schroeder’s commentary on the conviction of the ALPHV/BlackCat members was not merely a reposting of news; it was a forensic questioning of the narrative’s structural integrity.2
Her post highlighted a series of discrepancies that defy the standard logic of cyber prosecutions:
The Reduction of Charges: Why were “sophisticated” actors who committed multiple intrusions charged with a single count of conspiracy to interfere with commerce?
The Jurisdictional Leap: How does a court in Southern Florida hold dominion over residents of Georgia and Texas who worked for companies in Chicago and Atlanta?
The Missing Link: Who is the “Third Man,” and why has his identity been scrubbed from the headline announcements?
The Timeline Paradox: How were these actors identified and arrested in 2025 for crimes committed in 2023, long after the alleged dissolution of the BlackCat infrastructure?
Schroeder’s skepticism—capped with the provocative question of whether the public was being served “a side of Pravda”—reflects a broader anxiety. In an industry predicated on zero-trust architectures, the revelation that the “call was coming from inside the house” is destabilizing. It suggests that the vetting mechanisms of top-tier firms like Sygnia and DigitalMint have failed, and that the “white hat” community is more permeable to criminal corruption than previously admitted.
2.2 The “Pravda” Factor: Analyzing the Skepticism
Schroeder’s reference to Pravda—the former official newspaper of the Soviet Communist Party—invokes the concept of a curated reality, where the state presents a narrative that is technically accurate yet functionally misleading. In the context of the Goldberg prosecution, this suspicion is fueled by the stark contrast between the gravity of the betrayal and the sterility of the “single count” press release.
However, as this report will demonstrate, the “Pravda” element is likely a misinterpretation of federal prosecutorial tradecraft. The seemingly “missing” details—specifically regarding the third co-conspirator and the specific technical means of attribution—are characteristic of sealed proceedings involving cooperating witnesses. The DOJ is not manufacturing a lie; it is protecting an asset. The opacity is a feature of the investigation, not a bug in the narrative.
3. The Architects of Betrayal: Profiles in Malfeasance
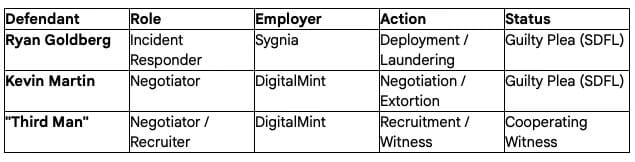
To understand the magnitude of this case, one must strip away the anonymity of the “cybercriminal” label and examine the specific professional identities of the defendants. Ryan Goldberg and Kevin Martin were not outsiders probing defenses; they were insiders holding the keys.
3.1 Ryan Goldberg: The Incident Responder
Ryan Goldberg, a 40-year-old resident of Georgia, held the position of Incident Response Manager at Sygnia.3
3.1.1 The Sygnia Context
Sygnia is not a generic IT support shop. It is a high-end cyber consulting and incident response firm, often associated with the most rigorous standards of security. Incident response (IR) firms are the “paramedics” of the digital world. When a Fortune 500 company is breached, they call Sygnia.
Privileged Access: An Incident Response Manager typically possesses “God-mode” privileges. To eradicate a threat, the responder must have deeper access than the attacker. They deploy Endpoint Detection and Response (EDR) agents, access domain controllers, and review sensitive logs.
The Betrayal: Goldberg’s role meant he understood exactly how investigations are conducted. He knew what logs were retained, what IP ranges were flagged as suspicious, and how long it took for security teams to triage an alert. By working as a BlackCat affiliate, he effectively weaponized this defensive doctrine. The DOJ noted he used his “sophisticated cybersecurity training and experience... the very type of crime that [he] should have been working to stop”.2
3.1.2 The Motivation and The Flight
What drives a well-paid professional at a top-tier firm to cybercrime? The investigation revealed a mundane but powerful motivator: debt. Goldberg admitted to authorities that “mounting personal debt” drove his decision to join the scheme.5 This highlights a critical failure in the “Insider Threat” monitoring of the cybersecurity industry—financial stress is a primary indicator of compromise, yet it appears to have gone unnoticed or unreported by his employer.
The consciousness of guilt was absolute. On June 27, 2025, mere days after being interviewed by the FBI, Goldberg and his wife boarded a one-way flight to Paris.3 He remained abroad for nearly three months, eventually attempting to travel from Amsterdam to Mexico City. It was in Mexico that the international law enforcement net closed, leading to his detention and extradition back to the United States.6 This flight serves as irrefutable evidence of his awareness of the criminality of his actions; innocent incident responders do not flee to Europe on one-way tickets after chatting with the FBI.
3.2 Kevin Martin: The Negotiator
Kevin Martin, 36, of Texas, was employed as a Ransomware Negotiator for DigitalMint.7
3.2.1 The DigitalMint Context
DigitalMint is a Chicago-based firm specializing in cryptocurrency enablement and, crucially, ransomware negotiation and settlement.
The Role of the Negotiator: In the ransomware economy, the negotiator is the intermediary. They advise the victim on how much to pay, communicate with the threat actor to verify proof of decryption, and facilitate the massive Bitcoin transfers required for settlement.
The Conflict of Interest: Martin’s position created a perverse incentive structure. As a negotiator, he had visibility into the “reservation price” of victims—the maximum amount a company was willing to pay to save their business. Operating as an affiliate, he could theoretically feed this intelligence to the BlackCat developers, ensuring that ransom demands were perfectly calibrated to extract the maximum possible amount without causing the victim to abandon the data.
The Irony: Martin was a public face of ethical negotiation, having previously given talks at law schools on negotiation ethics.9 His pivot to active extortion is a profound violation of the fiduciary-like trust placed in negotiators.
3.3 The “Third Man”: The Nexus in Land O’Lakes
Schroeder’s query rightly identifies the “specter of the third man” as a critical unresolved narrative arc. The research confirms his existence, his location, and his role, even if the DOJ press release sanitizes his name.
Location: Land O’Lakes, Florida.10
Role: He was the recruiter. The snippet 10 explicitly states that the two rogue employees (Goldberg and Martin) were recruited by the third, unnamed co-conspirator.
Employment: Like Martin, he was a ransomware negotiator at DigitalMint.7
Status: While Goldberg and Martin are awaiting sentencing, DigitalMint has publicly referred to this individual as a “cooperating witness” who is “not an investigative target” in the same docket.11
This status explains the “Pravda”-like silence. In federal conspiracy cases, the first participant to cooperate often pleads to a sealed information or receives a Non-Prosecution Agreement (NPA) in exchange for testimony. The Third Man’s role was likely to provide the chat logs, the encrypted communications (via Signal or Jabber), and the financial ledgers that linked the anonymous “affiliate” IDs on the BlackCat panel to the real-world identities of Goldberg and Martin. He is not missing; he is the prosecution’s star witness.
4. The Mechanism of Action: Inside the BlackCat Conspiracy
To understand the charges, one must understand the tool. ALPHV (BlackCat) was not just malware; it was a business.
4.1 The Ransomware-as-a-Service (RaaS) Model
BlackCat operated on a highly structured RaaS model, which separates the “product” from the “service.”
The Core (ALPHV Admins): Located primarily in Russia/CIS. They developed the ransomware (written in Rust, a modern programming language that offers memory safety and cross-platform compilation, allowing attacks on both Windows and Linux/ESXi environments). They maintained the Tor-based leak sites and the payment processing infrastructure.
The Affiliates (The Defendants): Independent contractors. They were responsible for:
Initial Access: Breaking into the victim network (or buying access from Initial Access Brokers).
Lateral Movement: Escalating privileges and moving across the network to locate critical data (Goldberg’s specialty as an Incident Responder).
Deployment: Encrypting the files.
Extortion: Managing the chat with the victim (Martin’s specialty as a Negotiator).
4.2 The 80/20 Split
The financial arrangement was strict. The plea agreement details that Goldberg and Martin agreed to pay the BlackCat administrators a 20% share of any ransoms, keeping 80% for themselves.12
The Economics: For the $1.2 million successful extortion, the Trio kept approximately $960,000, splitting it three ways (~$320,000 each). The remaining ~$240,000 was sent to the BlackCat core wallet.
4.3 The 2023 Campaign and the Exit
The malfeasance occurred in 2023.2 This was the operational zenith of BlackCat.
Targets: The group targeted over 1,000 victims globally, including major entities like Reddit and MGM Resorts.
The “Cat and Mouse” Game: In December 2023, the FBI launched Operation Grayskull, seizing the BlackCat websites and releasing a decryption tool that saved victims $99 million.14
The Retaliation: In a brazen act of defiance, the BlackCat administrators briefly “un-seized” their site and removed restrictions on affiliates, encouraging them to target hospitals and critical infrastructure. This led to the devastating attack on Change Healthcare in early 2024.
The Exit: Following the Change Healthcare attack and the intense law enforcement heat, the BlackCat admins performed an “exit scam”—they faked a law enforcement seizure of their own infrastructure to steal the affiliate’s share of the massive Change Healthcare ransom (rumored to be $22 million) and disappeared.
The Key Question: “If they haven’t been active, how were these cyber hackers found?”
The answer lies in the Operation Grayskull seizure. When the FBI infiltrated the BlackCat backend in late 2023, they didn’t just turn off the lights; they copied the databases.
Affiliate Panels: The FBI likely gained access to the “Affiliate Panel,” which tracks which affiliate ID is associated with which victim.
Chat Logs: Ransomware negotiations occur on chat portals hosted by the gang. The FBI seizure likely captured the history of negotiations conducted by Martin.
Cryptocurrency Trace: The $1.2 million payment from the Florida medical company was a tangible thread. Even with mixers, the combination of backend data (knowing which wallet belonged to the affiliate) and blockchain analytics allowed the FBI to trace the 80% split to wallets controlled by the defendants.
5. The Legal Anatomy: The Hobbs Act and the “Single Count”
A central pillar of the Schroeder’s skepticism is the legal framing: “So that is a single violation of the Hobbs Act? More specifically a conspiracy to do so... Next, there was a single count of malfeasance?”
This phrasing underestimates the severity and strategic utility of the Hobbs Act in federal cyber prosecutions.
5.1 18 U.S.C. § 1951: The Nuclear Option
The Hobbs Act, enacted in 1946, was originally designed to combat labor racketeering and highway robbery. It prohibits “actual or attempted robbery or extortion affecting interstate or foreign commerce.”
Why Hobbs and not CFAA? The Computer Fraud and Abuse Act (CFAA) is the primary anti-hacking statute, but it has limitations.
Penalties: A basic CFAA charge often carries a 5-year maximum.
The “Authorization” Quagmire: Following the Supreme Court’s Van Burendecision, defense attorneys can argue that an employee (like Goldberg) who had valid credentials did not “exceed authorized access” even if they used that access for malicious purposes.
The Hobbs Act Advantage: The Hobbs Act focuses on the extortion, not the hacking. It carries a 20-year maximum sentence.7 It simplifies the narrative for a jury: “They demanded money under threat of harm.”
The “De Minimis” Standard: To trigger the Hobbs Act, the government only needs to prove a “de minimis” (minimal) effect on interstate commerce. A ransomware attack that shuts down a medical company, preventing it from buying supplies from out of state or treating out-of-state patients, easily meets this bar.
5.2 The “Single Count” Strategy
The “single count” is not a sign of weak evidence; it is the hallmark of a Rule 11(c)(1)(C) Plea Agreement.
Stacking vs. Efficiency: The government could have charged them with 20 counts of Wire Fraud, 5 counts of CFAA violations, and Money Laundering. However, sentences often run concurrently.
The Deal: As explicitly stated in Snippet 7 , “the government agreed to dismiss counts two and three of the indictment at sentencing... involving interference with commerce by [other means].”
Outcome: The defendants plead to the count with the highest statutory maximum (Hobbs Act Conspiracy - 20 years), giving the judge full discretion to impose a severe sentence, while saving the government the cost and risk of a trial. It is a streamlined path to the same result: a decade-plus in federal prison.
5.3 The Conspiracy Charge
Charging Conspiracy (18 U.S.C. § 371 or § 1951(a)) is strategically vital.
Pinkerton Liability: Under the Pinkerton doctrine, every conspirator is liable for the substantive crimes committed by their co-conspirators in furtherance of the conspiracy.
The “Overt Act”: The government does not need to prove Goldberg typed the specific encryption command. They only need to prove he agreed to the plan and that one of them (perhaps the Third Man) did an overt act (like sending an email or renting a server). This nullifies the “I didn’t press the button” defense.
6. Jurisdictional Anatomy: The “Miami” Question
Schroeder asks: “How did they land up in a Miami federal court? One resided in Texas and one resided in Georgia?... The only thing that it appears to have jurisdiction over that comes to mind is Mar-a-Lago.”
This question touches on the complex concept of Federal Venue under 18 U.S.C. § 3237.
6.1 The Victim Nexus (The “Effects” Test)
In federal criminal law, venue is proper in any district where the offense was “begun, continued, or completed.”
The Florida Medical Company: The snippets confirm that one of the five victims—and the only one to pay the $1.2 million ransom—was a “Florida medical company”.3
SDFL Jurisdiction: While the exact name of the company is sealed, the filing in the Southern District of Florida (SDFL) confirms that this victim was located in Miami-Dade, Broward, Palm Beach, or the surrounding counties covered by the SDFL.
Completion of the Crime: The crime of extortion is “completed” when the victim parts with their property. Since the victim sent the $1.2 million from the Southern District, the crime occurred in the Southern District.
Electronic Reach: Even though Goldberg sat in Georgia and Martin in Texas, their digital extortion demands “reached into” the Southern District of Florida. This establishes venue.
6.2 The “Land O’Lakes” Complication
The Third Man resided in Land O’Lakes, Florida.
Geography: Land O’Lakes is in Pasco County, which falls under the Middle District of Florida (MDFL) (Tampa division), not the Southern District.
Why SDFL then?
The Victim Trumps the Co-conspirator: The location of the victim (SDFL) is often a stronger venue hook than the residence of a co-conspirator, especially for the extortion charge.
Investigative Lead: The FBI Miami Field Office led the investigation.2 Prosecutors generally file charges in the district where the investigating agents are based, provided there is a legal hook (the victim).
Operation Grayskull: The disruption of BlackCat was a major international operation coordinated largely out of major FBI cyber hubs. Miami is a primary hub for cybercrime involving Latin America and domestic ransomware.
6.3 Mar-a-Lago and the SDFL
Schroeder’s reference to Mar-a-Lago highlights the high-profile nature of the SDFL. It is, indeed, the same federal district that handles major national security cases (like the classified documents case). However, its jurisdiction over the Goldberg case is standard criminal procedure based on the “locus delicti” (scene of the crime)—which, in a ransomware case, is the server room of the victim who paid the bill.
7. The “Pravda” Commentary: Analysis of the Anomalies
Schroeder asks: “Are there some oddities here? And if there are, would anyone like a side of Pravda with that?”
This question speaks to the suspicion of a curated narrative. Let us audit the “Oddities.”
7.1 Oddity 1: The Missing Third Man
Observation: The recruiter is missing from the indictment.
Explanation: He is a Cooperating Witness. This is not a cover-up; it is standard operating procedure. If the DOJ named him, it would expose him to retaliation before he testifies or completes his cooperation against other targets (potentially the Russian core of BlackCat). The silence is tactical.
7.2 Oddity 2: The Timeline Gap (2023 vs. 2025)
Observation: Why announce it now if the crimes were in 2023?
Explanation:
The Flight: Goldberg fled the country in June 2025. The DOJ likely sealed the indictment to prevent Martin from also fleeing while they hunted Goldberg.
Extradition: Getting a defendant back from Mexico (where Goldberg was caught) takes diplomatic coordination.
Forensics: Tracing the $1.2 million through the blockchain to the defendants’ personal accounts (to prove they received the 80% split) is a time-consuming process that requires subpoenaing exchanges (KYC data).
7.3 Oddity 3: The “Single Count”
Observation: A massive cybercrime spree reduced to one count.
Explanation: As detailed in Section 5.2, this is a Plea Deal efficiency. The 20-year max of the Hobbs Act is sufficient. It is not a slap on the wrist; it is a sledgehammer disguised as a single sheet of paper.
7.4 The Real Anomaly: The Professional Betrayal
The only true “oddity” that defies explanation is the psychology of the defendants.
Sygnia and DigitalMint: These are not entry-level firms. They are the “Navy SEALs” of cyber defense and negotiation. For employees of these specific firms to defect is comparable to a DEA agent selling heroin.
The Debt Factor: The revelation that Goldberg was drowning in debt suggests a catastrophic failure of Continuous Vetting. In the intelligence community, financial distress is the #1 indicator of insider threat. The private cybersecurity sector, despite handling sensitive data, evidently lacks the rigorous financial monitoring required to flag a “high-risk” employee before they break bad.
8. Strategic Implications and Future Outlook
The Goldberg/Martin case will likely serve as a pivotal case study for the next decade of cybersecurity regulation and insurance.
8.1 The Death of Trust
The RaaS model relies on affiliates. Usually, these affiliates are anonymous actors in Eastern Europe. The revelation that they are actually US-based security professionals creates a “Zero Trust” crisis for the service industry.
Impact: Clients may now demand that Incident Response firms submit their employees to invasive financial auditing.
Insurance: Cyber insurance carriers, who rely on the assessments of IR firms and negotiators, may deny coverage if the firms cannot prove their employees are not complicit in the extortion.
8.2 The Rise of the “Insider Affiliate”
This case proves that the RaaS model has evolved. It is no longer just about “hackers vs. companies.” It is about criminal recruitment within the supply chain.
The “Third Man” in Land O’Lakes acted as a headhunter. He identified vulnerable colleagues (Goldberg with his debt) and recruited them into the conspiracy. This “criminal HR” function is a terrifying evolution of organized cybercrime.
8.3 The “Negotiator” Regulation
The unregulated nature of “Ransomware Negotiation” is likely to end. Kevin Martin’s ability to play both sides—advising the victim while extinguishing them—will likely lead to licensure requirements for negotiators, similar to private investigators or financial advisors, requiring background checks and fiduciary standards.
9. Conclusion
The conviction of Ryan Goldberg and Kevin Martin is not a story of “Pravda” or propaganda. It is a story of asymmetric betrayal.
The Department of Justice, utilizing the Hobbs Act, successfully pierced the anonymity of the ALPHV/BlackCat infrastructure—not by hacking the hackers, but by flipping the “Third Man” in Land O’Lakes and tracing the money back to the debts of a desperate man in Georgia.
The jurisdictional reach of the Southern District of Florida was legally secured by the location of the victim who paid the $1.2 million ransom. The “single count” is a strategic mechanism to ensure a swift, severe prison sentence without the vagaries of a trial.
Julie Schroeder’s initial query was prescient: there was more to the story. But the hidden layers were not state secrets; they were the ugly, mundane realities of greed, debt, and the fragility of trust in the digital age. The “Third Man” is singing, the “Guardians” are in handcuffs, and the industry is left to reckon with the enemy within.

Works cited
Julie Schroeder’s LinkedIn post, accessed January 9 2026, https://www.linkedin.com/posts/juliesaslowschroeder_cybersecurity-activity-7415219203680710656-C3Vj
Two Americans Plead Guilty to Targeting Multiple U.S. Victims Using ALPHV BlackCat Ransomware - Department of Justice, accessed January 9, 2026, https://www.justice.gov/opa/pr/two-americans-plead-guilty-targeting-multiple-us-victims-using-alphv-blackcat-ransomware
Ransomware responders plead guilty to using ALPHV in attacks on US organizations, accessed January 9, 2026, https://therecord.media/ransomware-responders-guilty-plea-using-alphv-blackcat-us-attacks
US cybersecurity experts plead guilty to orchestrating ALPHV ransomware attacks, accessed January 9, 2026, https://cyberinsider.com/us-cybersecurity-experts-plead-guilty-to-orchestrating-alphv-ransomware-attacks/
Cybersecurity Insiders Admit to Role in BlackCat Ransomware Campaign, accessed January 9, 2026, https://www.bitdefender.com/en-us/blog/hotforsecurity/cybersecurity-insiders-admit-to-role-in-blackcat-ransomware-campaign
Cyber Defenders Gone Rogue: Experts Charged in Ransomware Scheme | eSecurity Planet, accessed January 9, 2026, https://www.esecurityplanet.com/threats/cyber-defenders-gone-rogue-experts-charged-in-ransomware-scheme/
2 Cyber Pros Admit to Being BlackCat Ransomware Affiliates - BankInfoSecurity, accessed January 9, 2026, https://www.bankinfosecurity.com/2-cyber-pros-admit-to-being-blackcat-ransomware-affiliates-a-30415
Former incident responders plead guilty to ransomware attack spree | CyberScoop, accessed January 9, 2026, https://cyberscoop.com/incident-responders-plead-guilty-ransomware-digitalmint/
Strategic Implementation Plan for the Digital Operational Resilience Act (DORA), accessed January 9, 2026, https://www.compliancehub.wiki/strategic-implementation-plan-for-the-digital-operational-resilience-act-dora/
Risky Bulletin: US indicts two rogue cybersecurity employees for ransomware attacks, accessed January 9, 2026, https://risky.biz/risky-bulletin-us-indicts-two-rogue-cybersecurity-employees-for-deploying-ransomware/
US Prosecutors Say Cybersecurity Pros Ran Ransomware Operation - Insurance Journal, accessed January 9, 2026, https://www.insurancejournal.com/news/national/2025/11/04/846384.htm
Cybersecurity Industry Workers Plead Guilty to Ransomware Attacks | PYMNTS.com, accessed January 9, 2026, https://www.pymnts.com/news/security-and-risk/2025/cybersecurity-industry-workers-plead-guilty-to-ransomware-attacks/
Cybersecurity Insiders Admit to Role in BlackCat Ransomware Campaign - Bitdefender, accessed January 9, 2026, https://www.bitdefender.com/en-au/blog/hotforsecurity/cybersecurity-insiders-admit-to-role-in-blackcat-ransomware-campaign
Two cybersecurity experts plead guilty to running ransomware operation - CSO Online, accessed January 9, 2026, https://www.csoonline.com/article/4112400/two-cybersecurity-experts-plead-guilty-to-running-ransomware-operation.html
