- Pascal's Chatbot Q&As
- Posts
- The custodial power of the state has evolved into a vast, opaque logistics network capable of moving human bodies across borders, into “black sites,” and through detention archipelagos...
The custodial power of the state has evolved into a vast, opaque logistics network capable of moving human bodies across borders, into “black sites,” and through detention archipelagos...
...with minimal external visibility. This report investigates a technological counter-measure to this enforced silence: the development of Tamper-Proof Somatic Tracking Systems.
Somatic Witness: The Architecture of Counter-Custodial Surveillance in the Age of Disappearance
by Gemini 3.0, Deep Research. Warning, LLMs may hallucinate!
1. Introduction: The Crisis of Custodial Opacity
The contemporary geopolitical landscape is increasingly defined by the phenomenon of the “administrative disappearance.” In liberal democracies and authoritarian regimes alike, the custodial power of the state has evolved into a vast, opaque logistics network capable of moving human bodies across borders, into “black sites,” and through detention archipelagos with minimal external visibility. From the undocumented migrant detained by Immigration and Customs Enforcement (ICE) in the United States to the political dissident spirited away by security services in autocratic nations, the fundamental vulnerability remains the same: the severance of the digital tether.
Modern identity is extrinsic; it resides in the smartphone, the cloud account, and the communication network. When a state actor arrests an individual, the first procedural act is the confiscation of these devices, effectively erasing the subject from the digital map. This report investigates a technological counter-measure to this enforced silence: the development of Tamper-Proof Somatic Tracking Systems. The objective is to engineer a class of body-integrated technologies designed not for state control, but for familial sousveillance—a mechanism for families to maintain an immutable line of sight to their loved ones, regardless of incarceration, deportation, or device seizure.
This analysis explores the fictional yet scientifically grounded scenario of a “Witness Society,” where citizens preemptively weaponize their own biology to ensure accountability. It provides an exhaustive technical examination of the power systems, communication protocols, and concealment methodologies necessary to build a tracker that can survive the hostile electromagnetic and physical environment of a maximum-security detention facility. Furthermore, it details how such a distributed sensor network would expose the clandestine operations of agencies like ICE, revealing secret flight paths, undisclosed holding centers, and the hidden velocity of mass deportation.
2. The Operational Environment: Anatomy of the Black Box
To engineer a device capable of “bunker busting”—transmitting location data from within a custodial environment—one must first understand the formidable physical and electromagnetic barriers designed to prevent exactly this type of communication. A detention center is not merely a prison for bodies; it is a prison for signals.
2.1 The Electromagnetic Barrier: The Accidental Faraday Cage
Modern detention facilities, whether purpose-built prisons or retrofitted warehouses, present a hostile RF environment. The primary adversary is attenuation caused by construction materials.
Reinforced Concrete and Rebar: Most facilities are constructed of thick reinforced concrete. The steel rebar mesh embedded within the concrete acts as a crude Faraday cage, while the concrete itself, often holding moisture, absorbs radio frequency (RF) energy. Research indicates that signal transmission loss through reinforced concrete can range from 30 dB at 100 MHz to over 65 dB at 900 MHz.1 This attenuation creates “dead zones” where standard cellular signals (LTE/5G) cannot penetrate.
Frequency Dependence: The physics of attenuation dictates that higher frequencies suffer greater loss. The 2.4 GHz band used by Wi-Fi and Bluetooth is heavily absorbed by both building materials and human bodies, making it unsuitable for long-range transmission from deep inside a facility.2
Active Countermeasures (Jamming and MAS): Beyond passive shielding, facilities increasingly employ active denial systems.
Jamming: While illegal for commercial use in some jurisdictions, prisons often utilize jamming technology to flood cellular bands with noise, rendering contraband phones useless.4
Managed Access Systems (MAS): A more sophisticated approach involves “capturing” cellular signals. MAS mimics a cell tower, forcing all devices in the facility to connect to it. It then filters traffic, allowing only authorized (whitelisted) devices to connect to the external network while blocking all others.6 A tracker operating on standard cellular frequencies would be immediately identified and neutralized by an MAS.
2.2 The Intake Gauntlet: Screening and Detection
The second layer of defense is the intake processing of the detainee. A “tamper-proof” device must be either undetectable or irremovable during this phase.
Non-Linear Junction Detectors (NLJD): The most potent threat to covert electronics is the NLJD. Unlike metal detectors, which find conductive mass, NLJDs transmit a pure RF signal and listen for harmonic reflections. Any semiconductor junction (a diode or transistor found in all microchips) will distort the signal, returning a specific harmonic signature.8 An NLJD can detect a powered-off device, or even a disconnected circuit board, buried inside a mattress or, theoretically, a body.10
Radiological Screening:
Transmission X-Ray: ICE and prison systems routinely use chest X-rays for tuberculosis screening and full-body scanners for contraband detection.11 Metallic components (batteries, copper antennas) appear as high-contrast artifacts on these scans.
Millimeter Wave (mmWave): These scanners, common at airports, bounce waves off the skin to detect anomalies. They cannot penetrate the body, making subdermal implants invisible to them, but they are highly effective at detecting surface-mounted “smart patches” or tattoos.12
2.3 The “Tamper-Proof” Paradox
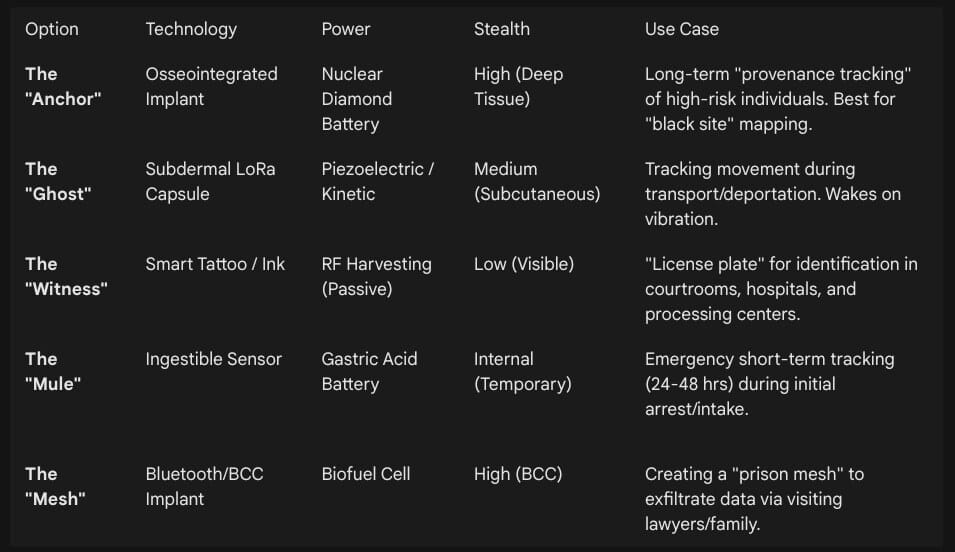
The term “tamper-proof” in a biological context is a misnomer. If a regime is determined enough, any device can be excised. Therefore, the operational definition of “tamper-proof” for this report is “asymmetric cost of removal.” The device must be integrated so deeply (e.g., osseointegration into the bone) that removing it requires major surgery, anesthesia, and recovery time—resources that a mass-deportation regime is unlikely to expend on thousands of detainees.14 The goal is to make the political and logistical cost of removing the tracker higher than the cost of allowing it to transmit.
3. Power Architectures: The Thermodynamic Constraints
The single greatest limiting factor for an implantable tracker is power. A standard GPS receiver requires approximately 30–50 milliwatts (mW) to acquire a signal from satellites.16 A cellular transmission requires pulses of up to 2 Watts. Standard lithium-ion batteries compliant with biological safety are too small to sustain this for months without recharging. We must look to exotic, “set-and-forget” power systems.
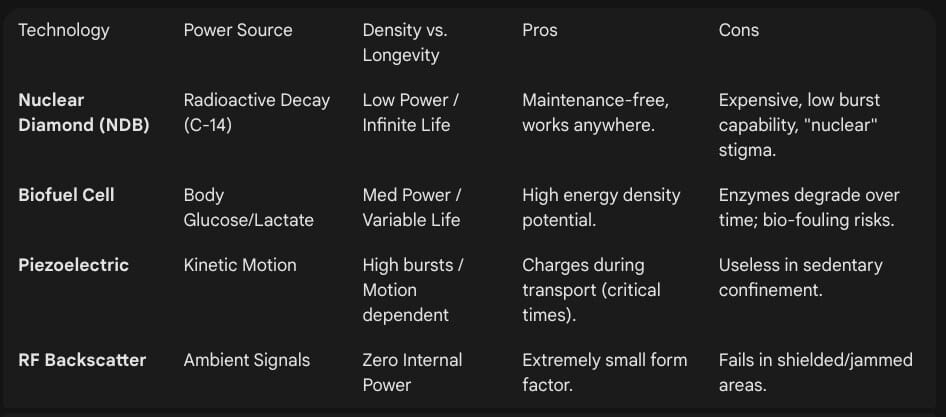
3.1 Nuclear Diamond Batteries (Betavoltaics)
The frontier of long-term, low-maintenance power lies in betavoltaic technology, specifically the “Nuclear Diamond Battery” (NDB). This technology creates a power source that is theoretically immortal in the context of a human lifespan.
3.1.1 Mechanism of Action
NDBs utilize the radioactive decay of isotopes such as Carbon-14 (C-14) or Nickel-63 (Ni-63). These isotopes emit beta particles (high-energy electrons) as they decay.
The Diamond Semiconductor: The radioactive source is encapsulated within synthetic diamond. Diamond is a wide-bandgap semiconductor. When beta particles strike the diamond lattice, they generate electron-hole pairs, creating an electric current.17
Safety: The diamond encapsulation acts as both the transducer and the shield. It prevents radiation leakage (C-14 beta radiation is weak and easily blocked by skin or plastic) and provides a chemically inert, biocompatible surface.19
3.1.2 The “Store-and-Burst” Architecture
The critical limitation of NDBs is power density. While they have immense energy density (total energy over time), their instantaneous power output is low—often in the range of microwatts ($\mu W$).21
Operational Cycle: An NDB cannot power a real-time GPS tracker. Instead, it serves as a trickle charger for a supercapacitor or solid-state battery. The device operates in a “deep sleep” mode (nanowatt consumption) for days or weeks, slowly accumulating energy. Once the capacitor is full, the device wakes up, acquires a location fix, fires a single high-power transmission burst (milliseconds long), and returns to sleep.
Implication: Families would not see a moving dot on a map. They would see a “provenance ping” once every 7 to 14 days. In a long-term detention scenario, this is sufficient to confirm the facility location.
3.2 Bio-Energy Harvesting: The Body as a Power Plant
To supplement the NDB or replace it in less invasive designs, the device can harvest energy from the host’s biological processes.
3.2.1 Biofuel Cells
Biofuel cells (BFCs) convert chemical energy from body fluids into electricity.
Glucose and Lactate: BFCs use enzymes (like glucose oxidase) coating the electrodes to oxidize glucose present in interstitial fluid or blood.23
Textile Integration: Recent advancements have produced yarn-based biobatteries using bacterial respiration, which can be woven into subcutaneous meshes. Scalability is achieved by arranging these yarns in parallel, potentially generating enough milliwatts to power low-energy Bluetooth beacons.24
3.2.2 Triboelectric and Piezoelectric Harvesting
Detainees are often moved—walked to interrogation, transported to buses, marched to aircraft.
Triboelectric Nanogenerators (TENGs): These devices harvest energy from friction and contact-separation between materials. A “smart tattoo” or subdermal patch can generate electricity from the stretching of skin during movement.25
Piezoelectric Ceramics: Implanted near joints or the heart, these convert mechanical strain into voltage.
Tactical Advantage: This harvesting method is activity-dependent. The device charges faster when the subject is being moved—precisely the moment when tracking data (location change) is most valuable.
3.3 Zero-Power Communication (RF Harvesting)
For scenarios where the subject is in an RF-rich environment (e.g., an airport terminal or a courtroom), Ambient Backscatter technology eliminates the need for internal power generation for transmission.
Mechanism: The device harvests energy from ambient TV, cellular, or Wi-Fi signals and modulates the reflection of these signals to communicate.26
Commercial Prototypes: OPPO’s “Zero-Power Tag” demonstrates the feasibility of tracking objects using only harvested environmental RF energy.28
Limitation: This fails in the “RF darkness” of a solitary confinement cell or a shielded transport van. It is a complementary technology, useful for exfiltrating data when the subject passes through public infrastructure.
4. The Communication Layer: Breaking the Faraday Cage
Once powered, the tracker must transmit data. The choice of frequency and protocol is the difference between a signal that dies in the skin and one that reaches a satellite.
4.1 Magnetic Induction (MI): The Bunker Buster
Standard radio waves (RF) interact with the electric dipoles in water and concrete, leading to absorption. Magnetic Induction (MI) communication relies on the magnetic near-field, which suffers minimal attenuation from non-magnetic materials like soil, water, and concrete.30
Through-the-Earth (TTE) Communication: Used in mining rescue operations, MI systems can transmit voice and data through hundreds of meters of solid rock.32
The Application: An MI-equipped implant operating at very low frequencies (LF or VLF, 3–30 kHz) could transmit a signal through the reinforced concrete walls of a detention center to a receiver buried in the ground outside or located in a parking lot.34
The Trade-off: The data rate is incredibly low (bits per second). The device cannot send audio or video. It can only send a “Heartbeat” containing a unique ID and a timestamp. But for a family, knowing “He is alive in Facility X” is the primary requirement.
4.2 LoRaWAN and the “Ghost” Network
For longer-range transmission when the subject is outdoors (e.g., in a recreation yard or on a tarmac), LoRa (Long Range) offers the best balance of range and power.
Deep Penetration: LoRa signals (Sub-GHz: 433/868/915 MHz) have superior penetration characteristics compared to cellular frequencies.35 A LoRa signal can penetrate deep into basements and urban canyons.
The “Gateway” Model: The family does not need to be near the prison. A distributed network of resistance-controlled LoRa gateways (cheap Raspberry Pi devices) placed on rooftops within 5–10 km of detention centers could listen for the faint “chirps” of implants.36
Burst Transmission: To avoid triangulation by authorities, the device uses “Chirp Spread Spectrum” (CSS) to send a signal below the noise floor, or bursts data in milliseconds.37
4.3 Body Channel Communication (BCC)
Body Channel Communication utilizes the human body itself as the transmission medium, turning the skin into a wire.38
Mechanism: The implant couples a signal (10–50 MHz) into the body’s conductive tissues. The signal propagates to the skin surface.40
Touch-Based Data Transfer: If a detainee shakes hands with a visitor, or touches a conductive surface (e.g., a metal table in a visitation room that has been instrumented with a receiver), the data is transferred instantly. This is the ultimate “covert channel,” requiring physical contact or extreme proximity, bypassing RF monitoring entirely.
4.4 Delay Tolerant Networking (DTN): The Data Mule
In the fictional “Witness Society,” the tracking infrastructure relies on Delay Tolerant Networking (DTN). This protocol is designed for intermittent connectivity.41
The “Bundle” Protocol: Data is not streamed; it is bundled. If a link is unavailable, the bundle sits in the implant’s memory.42
Epidemic Routing: The implant constantly scans for other devices—other detainees’ implants or visitors’ phones. When a connection is made (via BCC or short-range Bluetooth), the bundle is copied.
The “Mule”: A lawyer entering the prison carries a receiver. As they walk through the corridors, their device passively collects encrypted bundles from every detainee they pass. When the lawyer leaves the facility and reconnects to the internet, the bundles are uploaded to the cloud, decrypting the location history of hundreds of people simultaneously. This mimics the “Sneakernet” distribution of El Paquete Semanal in Cuba, where physical hard drives move data that the internet cannot.43
5. Stealth and Permanence: The “Tamper-Proof” Architecture
5.1 Osseointegration: The Permanent Anchor
To achieve true permanence, the device must become part of the body. Osseointegration is the direct structural and functional connection between living bone and the surface of a load-bearing implant.14
Surgical Procedure: Originally developed for amputees to attach prosthetics directly to the skeleton, this technique can anchor a tracking capsule inside the marrow cavity or attached to the cortex of the femur or humerus.45
Removal Barrier: Removing an osseointegrated device is not a simple excision; it is an orthopedic surgery requiring bone saws, risk of fracture, and significant rehabilitation.15 In a mass detention scenario, the state lacks the medical infrastructure to perform this on thousands of detainees. The device stays because removing it is too costly.
The e-OPRA System: Existing medical systems like e-OPRA already provide a bidirectional interface for permanent communication with implanted electrodes.14 Adapting this for a tracker provides a precedent for bio-integrated electronics.
5.2 Radiolucency: Evasion of X-Ray Detection
To delay detection during the initial intake screening, the device must be invisible to X-rays.
Radiolucent Materials: Traditional titanium casings are radio-opaque (visible white blobs on X-ray). The tracker must be encased in PEEK (Polyether ether ketone) or carbon-fiber-reinforced PEEK, which is radiolucent and widely used in spinal implants to allow post-op imaging.47
Carbon Electronics: Replacing copper wiring with Carbon Nanotubes (CNTs) or Graphene traces significantly reduces X-ray contrast. Graphene is atomically thin and practically invisible to standard medical X-ray imaging.49 A battery using carbon-based electrodes and a PEEK casing would appear as a faint shadow, easily mistaken for a cyst or scar tissue by a hurried technician.51
5.3 Smart Tattoos and Subdermal Ink
For a less invasive “tamper-evident” approach, Smart Tattoos offer a unique solution.
Technology: These are ultra-thin electronic meshes or graphene-based sensors applied to the skin or injected into the dermis.25 They can function as passive NFC tags.
The “License Plate” Concept: While they cannot house a large battery for GPS, they provide a permanent, machine-readable identity. If a detainee is processed through a scanner, the resistance network (hacking into the scanner feed) or a clandestine reader can log the ID.
Cultural Camouflage: These circuits can be designed to look like decorative tattoos, using conductive inks that blend with artistic designs, hiding in plain sight.53
6. Fictional Scenario: The “Equiveillance” Society
The prompt requests elaboration on a fictional situation where this methodology would exist. We posit a near-future society operating under a regime of “Soft Authoritarianism,” where disappearance is a bureaucratic tool.
6.1 The Rise of the “Witness Network”
In this society, trust in judicial process has collapsed. The “Right to Notification” 55 is a legal fiction; arrests result in administrative voids where individuals are lost in private prison systems for months. In response, a civil rights movement—The Equiveillance Collective—emerges. Their philosophy is based on Mann’s theory of Sousveillance (watching the watchers).56
Voluntary Chipping: Citizens do not wait to be tagged by the state; they tag themselves. The “Witness Chip” becomes a rite of passage for activists, immigrants, and vulnerable populations. It is an act of defiance: “You can take my body, but you cannot hide it.”
The Infrastructure: The network is sustained by “Keepers”—volunteers who host LoRa gateways in their attics and businesses near prisons, creating a decentralized coverage map that monitors the dark zones of the state.
6.2 The “Ghost Flight” Watcher
The system’s primary value is revealed in the tracking of deportation logistics, specifically ICE Air Operations.
Scenario: A specialized “Black Box” implant (Osseointegrated, NDB-powered) is carried by a high-value dissident.
Detection: The device’s accelerometer detects the specific vibration signature of an aircraft takeoff. It wakes, acquires a GPS lock through the airplane window, and stores the coordinate.
Exfiltration: Upon landing at a secret rendition site or a remote airfield, the device fires a high-power LoRa burst.
The Leak: The data creates a “Strava-like” heatmap.58 Just as fitness trackers inadvertently revealed US military bases, the aggregate data of thousands of deported migrants reveals the secret flight paths, refueling stops, and “black sites” used by the regime. This data is published on the decentralized web, forcing the government to acknowledge the sheer scale of its operations.
7. Exposure of Controversial Activities
The deployment of such technology would fundamentally alter the visibility of state violence.
7.1 Mapping the Archipelago of Detention
Currently, facilities like the “Alligator Alcatraz” in the Florida Everglades can appear overnight, bypassing local oversight and environmental review.59 An active tracking network would identify these sites immediately.
Anomaly Detection: A cluster of signals suddenly appearing in a swamp or a desert warehouse alerts the network.
Conditions Monitoring: Biosensors in the implants (powered by the same NDB/Harvesting system) could broadcast biometric distress—elevated heart rates, signs of malnutrition, or hypothermia—providing real-time data on the conditions of confinement, not just the location.61
7.2 The Politics of Evidence
The data becomes a legal weapon.
Habeas Corpus: Lawyers no longer need to ask “Where is my client?” They present a geospatial log: “My client is in Cell Block D of Facility 4.”
Human Rights Accountability: The “Data Mules” exfiltrating bundles from prisons provide logs of movement that contradict official narratives. If a detainee dies in custody, the implant’s temperature and heart rate logs provide a forensic timeline of death, preventing the state from falsifying the time or cause.62
8. Ethical and Legal Complexities
8.1 The Privacy Paradox
The “Witness Society” requires a radical surrender of privacy. To be safe from the state, the individual must become transparent to the Network.
The Double Agent: The state could theoretically hack the resistance network. If the encryption keys are compromised, the “freedom tracker” becomes the ultimate tool of totalitarian control, allowing the state to map not just the prisoner, but their entire social graph (the families and lawyers who visit them).63
Coercion: There is a risk that families might force this technology on children or elderly relatives “for their own safety,” mirroring the very control dynamics they seek to escape.
8.2 The Normalization of the Cyborg
By normalizing the implantation of tracking hardware, the resistance paves the way for the state to eventually mandate it. If “good citizens” chip themselves to stay safe, the state can argue that “bad citizens” must be chipped to keep society safe. The technology is neutral; its application is political.64
9. Detailed Technological Options Matrix
10. Conclusion
The vision of a tamper-proof tracker for the “disappeared” is technically feasible only through a convergence of extreme technologies: Nuclear Diamond Batteries for immortality, Magnetic Induction for wall-penetration, Osseointegration for permanence, and Delay Tolerant Networking for resilience.
This architecture creates a Somatic Witness—a body that testifies to its own location and condition regardless of the state’s attempt to silence it. While the ethical risks of a “surveillance-for-safety” trade-off are immense, in a fictional or future scenario where the rule of law has fractured, such a system represents the last line of defense against the administrative void. It forces the state to operate in the light, turning the bodies of the incarcerated into the beacons of their own liberation.

Works cited
Investigation of RF transmission properties of human tissues - Semantic Scholar, accessed December 28, 2025, https://pdfs.semanticscholar.org/2375/c6c20d1e2a7e063c41a5e2ee0ae117259431.pdf
RF Channel Modeling for Implant-to-Implant Communication and Implant to Subcutaneous Implant Communication for Future Leadless Cardiac Pacemakers - PubMed, accessed December 28, 2025, https://pubmed.ncbi.nlm.nih.gov/29993450/
Analysis of Radio Propagation Inside the Human Body for in-Body Localization Purposes - UT Student Theses, accessed December 28, 2025, https://essay.utwente.nl/fileshare/file/66071/Dove_MA_TE.pdf
Cell Phone Jamming Technology for Contraband Interdiction in Correctional Settings | Urban Institute, accessed December 28, 2025, https://www.urban.org/sites/default/files/2023-07/Cell%20Phone%20Jamming%20Technology%20for%20Contraband%20Interdiction%20in%20Correctional%20Settings.pdf
September 9, 2025 FCC FACT SHEET* Promoting Technological Solutions to Combat Contraband Wireless Device Use in Correctional Fac, accessed December 28, 2025, https://docs.fcc.gov/public/attachments/DOC-414416A1.pdf
Contraband Cell Phones in Prisons - National Telecommunications and Information Administration, accessed December 28, 2025, https://www.ntia.gov/files/ntia/publications/contrabandcellphonereport_december2010.pdf
Managed Access Systems Can Prevent Contraband Cellphone Use, accessed December 28, 2025, https://nij.ojp.gov/topics/articles/managed-access-systems-can-prevent-contraband-cellphone-use
Non Linear Junction Detector - Phantom Technologies, accessed December 28, 2025, https://phantom-technologies.com/detection-electronic-devices/
Non-Linear Junction Detectors (NLJDs) - Detect Electronic Devices, accessed December 28, 2025, https://reiusa.net/nljd/
NLJD Prison April 26 07.indd, accessed December 28, 2025, https://www.ntia.gov/files/ntia/rei-orion-nljd-detects_cell_phones_in_prisons.pdf
insdetention standard | ice, accessed December 28, 2025, https://www.ice.gov/doclib/dro/detention-standards/pdf/medical.pdf
Rohde & Schwarz security screening solutions, accessed December 28, 2025, https://www.rohde-schwarz.com/us/solutions/security/security-screening/security-screening_255126.html
How Millimeter Wave Scanners Work - Science | HowStuffWorks, accessed December 28, 2025, https://science.howstuffworks.com/millimeter-wave-scanner.htm
Study Details | NCT06391697 | Magnetic Bead Tracking System and eOPRA Implant System With Bionic Prosthesis for Transtibial Amputees | ClinicalTrials.gov, accessed December 28, 2025, https://clinicaltrials.gov/study/NCT06391697
Osseointegration FAQs - Walter Reed National Military Medical Center, accessed December 28, 2025, https://walterreed.tricare.mil/Health-Services/Hospital-Care-Surgery/Osseointegration/Osseointegration-FAQs
Is it possible to track someone’s GPS location with a subdermal implant? - Reddit, accessed December 28, 2025, https://www.reddit.com/r/AskTechnology/comments/49deca/is_it_possible_to_track_someones_gps_location/
Nuclear Diamond Batteries Inc., accessed December 28, 2025, https://www.nucleardiamondbatteriesinc.com/
Carbon-14 diamond battery is world first, say UK scientists, accessed December 28, 2025, https://www.world-nuclear-news.org/articles/carbon-14-diamond-battery-is-world-first-say-uk-scientists
A diamond battery for Valentine’s Day? - American Nuclear Society, accessed December 28, 2025, https://www.ans.org/news/2025-02-14/article-6765/a-diamond-battery-for-valentines-day/
Diamonds are forever? World-first carbon-14 diamond battery made - GOV.UK, accessed December 28, 2025, https://www.gov.uk/government/news/diamonds-are-forever-world-first-carbon-14-diamond-battery-made
Nuclear diamond batteries - ScienceForSustainability, accessed December 28, 2025, https://scienceforsustainability.org/wiki/Nuclear_diamond_batteries
Diamond battery - Wikipedia, accessed December 28, 2025, https://en.wikipedia.org/wiki/Diamond_battery
Powering Implantable and Ingestible Electronics - PMC - PubMed Central - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC8553224/
Energy Harvesting in Implantable and Wearable Medical Devices for Enduring Precision Healthcare - MDPI, accessed December 28, 2025, https://www.mdpi.com/1996-1073/15/20/7495
Smart Tattoo Sensors 2.0: A Ten-Year Progress Report through a Narrative Review - PMC, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC11048663/
Ambient Backscatter: Wireless Communication Out of Thin Air - University of Washington, accessed December 28, 2025, https://homes.cs.washington.edu/~gshyam/Papers/amb.pdf
Ambient Backscatter: Wireless Communication Out of Thin Air - Embedded, accessed December 28, 2025, https://www.embedded.com/ambient-backscatter-wireless-communication-out-of-thin-air/
Oppo Zero-Power Tag Tracker Prototype is Now Here, No More Batteries - Tech Times, accessed December 28, 2025, https://www.techtimes.com/articles/288354/20230228/oppo-zero-power-tag-tracker-prototype-now-here-more-batteries.htm
OPPO Zero-Power Tag is Named to TIME’s List of Best Inventions of 2023 for Envisioning a More Sustainable Future, accessed December 28, 2025, https://www.oppo.com/en/newsroom/press/oppo-zero-power-tag-time-best-inventions/
[2510.14854] Through-the-Earth Magnetic Induction Communication and Networking: A Comprehensive Survey - arXiv, accessed December 28, 2025, https://arxiv.org/abs/2510.14854
accessed December 28, 2025, https://www.researchgate.net/publication/224133041_Magnetic_Induction_Communications_for_Wireless_Underground_Sensor_Networks#:~:text=Magnetic%20induction%20(MI)%20communication%20is,soil%2C%20concrete%2C%20and%20metals.
Magneto-Inductive NEtworked Rescue System (MINERS): Taking sensor networks underground | IEEE Conference Publication | IEEE Xplore, accessed December 28, 2025, https://ieeexplore.ieee.org/document/6920946/
NIOSH-Sponsored Research in Through-the-Earth Communications for Mines - CDC Stacks, accessed December 28, 2025, https://stacks.cdc.gov/view/cdc/227384/cdc_227384_DS1.pdf
Magneto-Inductive NEtworked Rescue System (MINERS): Taking Sensor Networks Underground, accessed December 28, 2025, https://www.cs.ox.ac.uk/files/4814/ipsn_markham.pdf
Feasibility of LoRa for Smart Home Indoor Localization - MDPI, accessed December 28, 2025, https://www.mdpi.com/2076-3417/11/1/415
LoRa Enabled GPS Tracker with ESP8266 & Nuvoton N032LE3AE - Campus Component, accessed December 28, 2025, https://www.campuscomponent.com/blogs/post/lora-enabled-gps-tracker-with-esp8266-nuvoton-n032le3ae
Feasibility of Backscatter Communication Using LoRAWAN Signals for Deep Implanted Devices and Wearable Applications - MDPI, accessed December 28, 2025, https://www.mdpi.com/1424-8220/20/21/6342
Analysis of the Human Body as an Antenna for Wireless Implant Communication, accessed December 28, 2025, https://ieeexplore.ieee.org/document/7399705/
Wireless communication with implanted medical devices using the conductive properties of the body - PMC - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC4156009/
Body Channel Based Wireless Power Transfer Method for Implantable Bioelectronics, accessed December 28, 2025, https://ieeexplore.ieee.org/document/9401654/
Delay-tolerant networking - Wikipedia, accessed December 28, 2025, https://en.wikipedia.org/wiki/Delay-tolerant_networking
Delay Tolerant Networking for Sensor Networks - DiVA portal, accessed December 28, 2025, http://www.diva-portal.org/smash/record.jsf?pid=diva2:1041559
El Paquete Semanal - Julia Weist, accessed December 28, 2025, https://work.deaccession.org/el-paquete-semanal/
El Paquete Semanal - Wikipedia, accessed December 28, 2025, https://en.wikipedia.org/wiki/El_Paquete_Semanal
Bone-Anchored Devices that Permanently Pass Through the Skin to Maximize Amputee Function - Discovery and Innovation at University of Utah Health, accessed December 28, 2025, https://discovery.med.utah.edu/2019/bone-anchored-devices-that-permanently-pass-through-the-skin-to-maximize-amputee-function/
Osseointegration for Lower and Upper Limbs - Medical Clinical Policy Bulletins | Aetna, accessed December 28, 2025, https://www.aetna.com/cpb/medical/data/1000_1099/1045.html
RELIEVE™ Radiolucent Laminoplasty System | Globus Medical, accessed December 28, 2025, https://www.globusmedical.com/products/relieve/
Radiolucent Structural Materials for Medical Applications, accessed December 28, 2025, https://www.mddionline.com/materials/radiolucent-structural-materials-for-medical-applications
Graphene Offers X-Ray Photoelectron Spectroscopy a Window of Opportunity | NIST, accessed December 28, 2025, https://www.nist.gov/news-events/news/2014/12/graphene-offers-x-ray-photoelectron-spectroscopy-window-opportunity
A Perovskite-Graphene Device for X-ray Detection - PMC - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC10688579/
A carbon nanotube x-ray source array designed for a new multisource cone beam computed tomography scanner - PMC - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC12303160/
Electronic Tattoos: Revolutionizing Healthcare and Biometric Tracking | by Sandra G | The Deep Hub | Medium, accessed December 28, 2025, https://medium.com/thedeephub/electronic-tattoos-revolutionizing-healthcare-and-biometric-tracking-2ffb119c2fe5
They Created Tattoos That Track You Without a Device - YouTube, accessed December 28, 2025
Stressed or Bored at Work? New Electronic Tattoo Can Help, accessed December 28, 2025, https://cockrell.utexas.edu/news/stressed-or-bored-at-work-new-electronic-tattoo-can-help/
Victim Notification | Help for Victims | OVC, accessed December 28, 2025, https://ovc.ojp.gov/help-for-victims/victim-notification
Sousveillance - P2P Foundation Wiki, accessed December 28, 2025, https://wiki.p2pfoundation.net/Sousveillance
Sousveillance and Surveillance: What kind of future do we want? - Philosophical Disquisitions, accessed December 28, 2025, https://philosophicaldisquisitions.blogspot.com/2014/10/sousveillance-and-surveillance-what.html
Militaries Race to Cover their Tracks in Light of Strava Scandal - AIIA, accessed December 28, 2025, https://www.internationalaffairs.org.au/australianoutlook/strava-heatmap-exposes-military-bases/
Florida’s Secretive Immigration Detention Center, Explained - ACLU of Oregon, accessed December 28, 2025, https://www.aclu-or.org/news/floridas-secretive-immigration-detention-center-explained/
Florida’s Secretive Immigration Detention Center, Explained | American Civil Liberties Union, accessed December 28, 2025, https://www.aclu.org/news/immigrants-rights/floridas-secretive-immigration-detention-center-explained
Beyond Tissue replacement: The Emerging role of smart implants in healthcare - PMC - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC10507164/
Current state of the art and future directions for implantable sensors in medical technology: Clinical needs and engineering challenges - PMC - NIH, accessed December 28, 2025, https://pmc.ncbi.nlm.nih.gov/articles/PMC10539032/
Digital Threat Modeling Under Authoritarianism - Schneier on Security, accessed December 28, 2025, https://www.schneier.com/blog/archives/2025/09/digital-threat-modeling-under-authoritarianism.html
The Rise of Preemptive Bans on Human Microchip Implants, accessed December 28, 2025, https://carnegiecouncil.org/media/article/preemptive-bans-human-microchip-implants
Fear, Uncertainty, and Doubt about Human Microchips | Strategic Technologies Blog - CSIS, accessed December 28, 2025, https://www.csis.org/blogs/strategic-technologies-blog/fear-uncertainty-and-doubt-about-human-microchips
GPS Implant for Livestock Tracking – Is It Feasible? : r/arduino - Reddit, accessed December 28, 2025, https://www.reddit.com/r/arduino/comments/1ihua0p/gps_implant_for_livestock_tracking_is_it_feasible/